Among the many free network scanning tools obtainable, zenmap is a very valuable tool that enables you to map out the entire network of your computer. The program is also talented to provide you with the topology map of the network. It will also give you the option to arrange the scan options.
What is Zenmap?
Whether you are a beginner or a progressive user, zenmap download will provide you with all the features you need to behavior a thorough network scan. Using this tool, you can easily create a network topology map and comparation the results of different scans. It also delivers detailed information on all the hosts and services on the network.
Vulnerability Assessment Scans
When you use zenmap, you can also achieve network vulnerability assessment scans. You can also save scan results and track changes. This makes zenmap download a great tool for busy network managers. Moreover, it allows you to create and use custom scanning profile auto-systemic networks. It also has the aptitude to perform auto-system scans.
Interactive Graphical Map
Besides, zenmap provides an communicating graphical map of the network. You can also zoom in on a specific host and view its details. You can also compare the results of two scans and make changes to the scan settings. You can also edit interfaces and view the IP addresses of hosts.
Option for Small Businesses
zenmap is a free tool that is also open source. It’s a decent option for small businesses that don’t have the resources to purchase network monitoring tools. You can also use it to achieve reconnaissance on a live production network.
How to Install Zenmap on Windows?
Using the zenmap package you can easily install a graphical user interface for Nmap. This makes Nmap easier for beginners, as well as experienced users.
Open-Source Tool
zenmap is a free, open-source tool that helps users perform scans on local networks and monitor traffic. It is a cross-platform tool that supports Windows, Mac, and Linux. It comprises a command creator, advanced tools, and a fisheye mode.
- zenmap can be downloaded on Windows. It is obtainable in both 64-bit and 32-bit versions. It can be found in the Windows store and in the Taskbar.
- zenmap is a cross-platform tool that offers a free graphical user interface for Nmap. It is designed to make Nmap easier for beginners, and offer progressive features for experienced users.
Intuitive Graphical Interface
zenmap can be downloaded and installed on Windows 10 and later versions. After downloading it, you can install it as an advantaged user or a non-privileged user. It has an intuitive graphical line that makes scanning and managing networks easier.
- When you install the package, you can select to install only the graphical user interface or the full package, which contains the Nmap CLI. The Nmap CLI is the command line version of the program.
Features of ‘Zenmap’
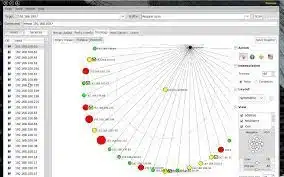
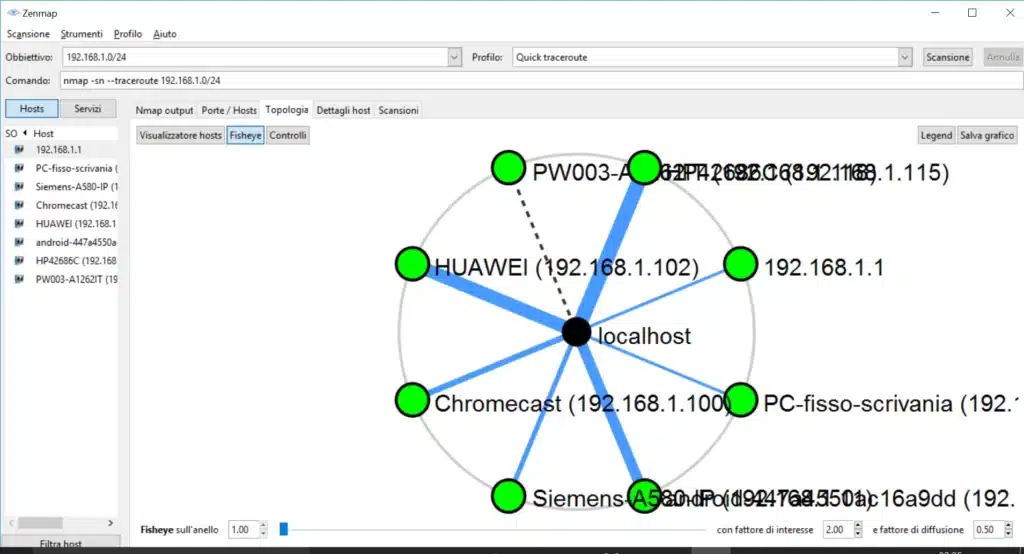
Among the many features of zenmap, one of the most exciting ones is its ability to create a topology map of a network. This allows you to see the connectivity and status of all of the hosts and plans on your network.
- It also allows you to save scan results in a searchable database.
- This makes it easy to control what has changed from one scan to the next.
- This is especially helpful for busy network managers.
- Another feature is the skill to detect the type of service a host is performing. This is helpful if you’re looking to path down a new service or determine whether an existing service is running properly. You can also opinion the host’s ports.
- Its ability to determine the type of OS a host is running. It also delivers an OS fingerprint, which identifies the software version,n, vendor and uptime.
- Interesting feature of zenmap is the aptitude to detect if a host is using a service that is known to be susceptible to a security attack. This feature is also useful if you want to ensure that your firewall is operating correctly.
- Another cool feature of zenmap is the ability to find out which requests are running on a host. This is especially helpful if you’re looking to identify potential susceptibilities in applications.
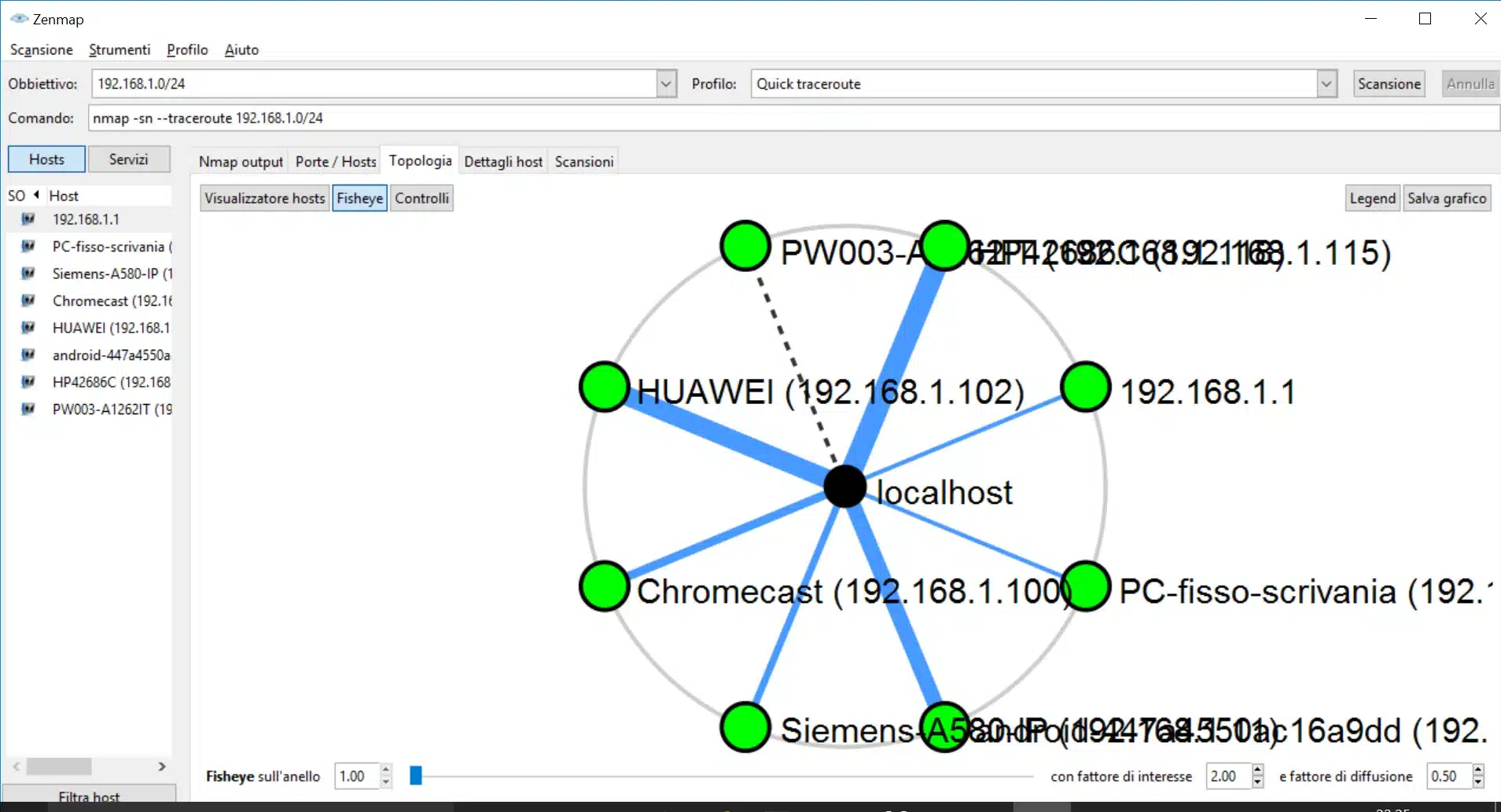
Topology Map of Network in Zenmap
Using the zenmap topology map, you can imagine how your network is laid out. It’s interactive, so you can zoom in and out. Depending on the size of your network, you can increase it by clicking on the Zoom and Ring Gap sliders.
Color Conventions
The topology map uses color agreements to display network paths. The thickness of a line is relative to the round-trip time. Orange lines indicate alternate paths. Each additional ring represents one more network hop.
Nmap command line tool
zenmap is a free, graphical interface for the Nmap command line tool. It’s calculated for security administrators. It’s easy to use and has a very short learning curve. It has the aptitude to save scans and templates. It also offers a contrast feature to allow users to compare results from different scans.
- The topology map of your network is an collaborating tool that can help you find security issues on your network. You can zoom in and out, add or remove hosts, and drag and resize the map.
Traceroute Information
zenmap also provides traceroute information that can be added to your network inventory. The traceroute information is added by perusing the network. If you want to include a certain protocol, select it in the protocols list.
High Ranking Keywords
macos nmap , nmap scan time , nmap scan udp , nmap version scan , nmap version detection , nmap fin scan , nmap ping , mac nmap , nmap operating system , nmap osx , nmap scan udp ports , nmap mac os , ssl-enum-ciphers nmap , nmap -s option . nmap scan dns , nmap udp port scan, nmap samba , nmap os , nmap icmp , nmap ftp scan , nmap export to csv, banner grabbing nmap , nmap database , nmap udp port.
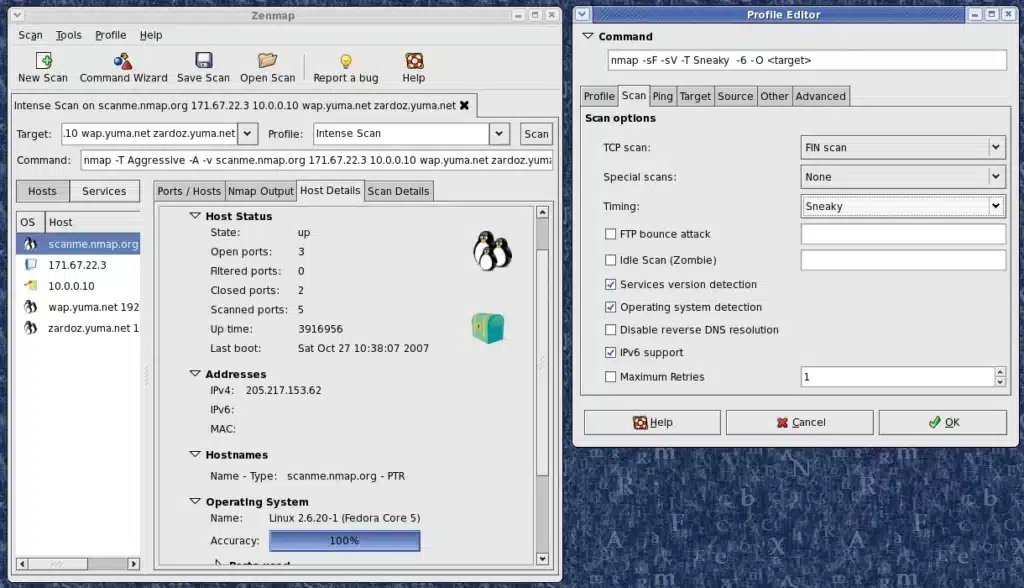
Configuring Zenmap Scan Options
Using a graphical user interface (GUI) to configure zenmap scan choices is a great way to streamline the process. This way you can rapidly check the health of your network and see how your devices are performing without the hassle of logging in to a command line interface.
- It’s also easy to save scans as profiles for later orientation. Using a profile makes it possible to perform the same scan multiple times, saving you time and effort.
- In addition to the Profile Editor, there’s also a New Profile feature. This is a command that you can use to launch a new profile, or you can physically type Ctl+P to bring up the command line.
- The Profile Editor also gives you the ability to name, describe and print out a scan profile. You can do this by clicking on Profile on the main toolbar.
Nmap Engine Works
The profile is a mixture of all the features of Nmap. It includes features such as service/version detection, host discovery, and a scan order. It’s a great way to get a feel for how the Nmap engine works and what options it supports.
Regular Output
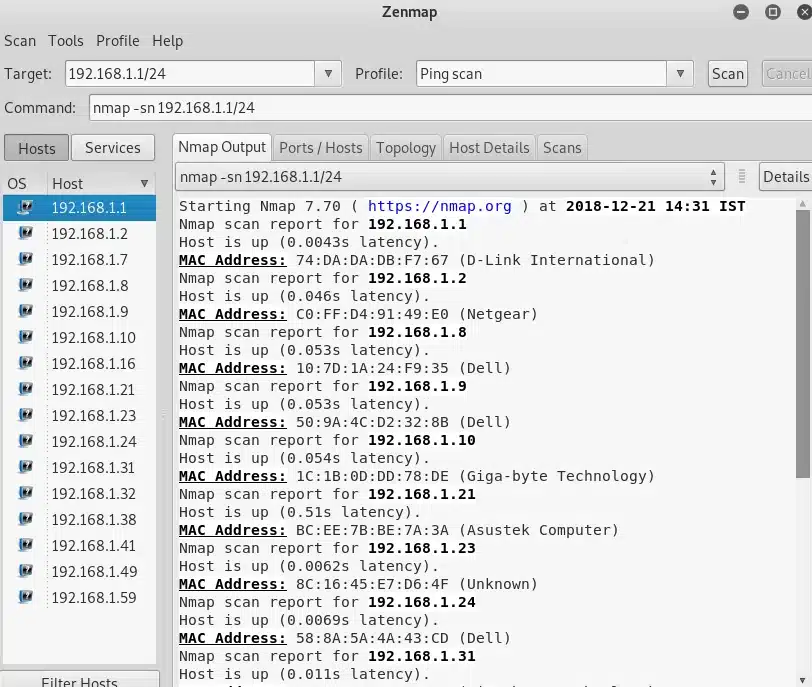
Besides the Profile Editor, you can also see how Nmap works by viewing the regular output. This output displays a host’s IP address, the number of open ports, and the status of scanned ports. The -T4 and -F flags are also visible on the output.
Is Zenmap Better Than Nmap?
Using zenmap is a great way to streamline your scanning tasks. It helps you identify host types, services, and port configurations. It can also assist you with patch organization efforts. The software is easy to learn and safe to use.
Open-Source Network Scanner
zenmap is a free, open-source network scanner for Windows, Linux, and OS X. It can scan networks and find devices, services, and vulnerabilities. Its graphical interface allows users to view topology maps, compare scans, and save scan results. It also features command profiles, allowing repeatable scans.
- Nmap has been around for twenty-five years, but its latest version, zenmap, has made it easier to use. This GUI application lets users to scan a network and rapidly configure scans.
Detect The Operating System
zenmap can notice the operating system (OS) of a host, as well as related software versions. It can also identify uptime and vendor information. It can also provide network topology maps. It can also provide a summary of a complete scan.
Searchable Database of Scans
With zenmap, you can save scan results, and compare them with preceding scans. You can also search through a searchable database of scans. You can use the results to classify what changed. zenmap can also help you find new hosts. It can also help you track services and ports on existing hosts.
Network Security Assessment
Using zenmap for your network security valuation is a great way to ensure that you are doing a thorough job of checking your systems for vulnerabilities. You will also be able to use it to recognize versions of operating systems, port scanning, and service fingerprinting.
GUI Version of Nmap
Associated to the command-line tool Nmap, the GUI version, zenmap, makes Nmap easier to use for beginners. It also allows you to save scans and compare results. nmap scan udp port , udp scan nmap , nmap banner grab , nmap portable , script args nmap , nmap powershell , nmap book , nmap -sv flag , nmap verbose , powershell nmap . nmap ssl-enum-ciphers , nmap ss , fin scan nmap , nmap fingerprint , nmap discovery scan, nmap install mac , is nmap illegal , mac install nmap ,nmap tcp/ip fingerprint In addition, it offers a lot of advanced features, making it useful to knowledgeable users as well.
In the past, Nmap required a lot of training and expertise to use. It also required knowledge of non-graphical interfaces. However, zenmap GUI makes it easier to tell Nmap what to find and how to find it.
Command Profile
You can use the GUI to run a scan, create a command profile, and save scans as profiles. You can also compare results and save them to a database. You can also run a scan recurrently, saving the results of each scan in separate profiles. The results of multiple scans can be compared and combined to display the results at once.
Zenmap Port Scanning Tool
Using the Zenmap port scanning tool, you can test your system against vulnerabilities. It is a multi-platform free open-source application. If you are a network security professional, this tool is a valued addition to your arsenal of tools. Its easy-to-use interface makes it easy for you to tell Nmap what you want to discover. Using a searchable database, you can compare your results.
- Port scanning is a fun and informative activity. It shows you the services running on your network. However, you need to understand a few things before you can use Nmap.
Private or Dynamic Port Numbers
The first thing you need to know is what ports to scan. The most common services on the Internet use TCP and UDP port numbers. However, some of them run on private or dynamic port numbers. In these cases, the IANA manages the port numbers. The IANA registers port numbers in order to ensure universal compatibility across the global internet.
Service fingerprinting
Using nmap -a service fingerprinting functionality, you can rapidly determine if a host is running any specific service on an open port. If the host is running a service, you can then follow up by sending a probe to that service. Then, nmap mac will try to match the data to its signatures.
Most Popular Network Discovery Tool
n a m p is the world’s very popular network discovery tool. nmap ping sweep has a number of features, counting host discovery, service detection, and susceptibility detection. install nmap on macbook is also extensile through scripts. In addition, nmap ping scan can adapt to network conditions during a scan.
Service Fingerprinting Function
The nmap udp scan service fingerprinting function is based on a folder of operating system signatures. nmap os detection database includes hundreds of different operating systems. When a host matches a fingerprint, nmap udp scanning prints a special ASCII-encoded version of that fingerprint.
Top Ranking Keywords
nmap udp , nmap os detect , nmap -so , port scanner mac , nmap for mac , host discovery nmap , nmap syn scan .nmap macos , nmap scan types , what is zenmap , download zenmap , nmap output , nmap filtered , nmap flag , nmap ipv6 , nmap xmas scan , ncat nmap , nmap os scan , nmap ncat , nmap ssl-enum-ciphers tls 1.3 , nmap scripting engine, nmap taking a long time, nmap macbook . install nmap on mac ,nmap on mac , nmap arp scan , nmap samba script , nmap ssl enum ciphers , ping scan nmap.
Identifying versions of operating systems
- Classifying versions of operating systems is important if you want to make the most of a network security scan. zenmap also very important if you want to detect a known security flaw in a system.
There are a few different methods to perform this task. Some of them are more precise than others. Depending on the circumstances, you may or may not be able to detect forms of operating systems using a particular tool.
Most Accurate Methods
One of the most accurate methods is using a tool called installing nmap on mac. This tool uses TCP/IP fingerprinting to detect the working system on a host. install nmap mac has over 2,000 IP fingerprints in its database. os detection nmap then comparations the response of the host to its internal database of over 2,600 operating systems.
Sophisticated Algorithm
Another tool that is worth looking into is p0f. This tool uses a urbane algorithm to detect operating systems. Unlike nmap web xml, p0f can also be used behind a firewall, which allows you to track down vulnerable machines.
Stealth Scan
Using Nmap to perform nmap operating system detection can help to avoid discovery by Intrusion Detection Systems. This technique can also help pen testers get closer to the target. There are some nmap detect os techniques obtainable from detect os nmap, each with its own advantages and disadvantages.
Determine a Target’s Operating System
The most basic scan is used to determine a target’s operating system by intreating a response from each host. During the scan, a series of TCP packets are sent to the target, allowing nmap stealth scan to fold information. The response is then analyzed and likened to a database of over 2600 operating systems.
Other Stealth Scan Techniques Include:
TCP SYN Scan: This scan uses a changed two-way handshake to zenmap establish a connection. The first step in the process is an SYN packet from the client to the target, while the second step is an ACK packet from the target to the client.
Getting More Information
The Island Boys Net Worth 2022, Bio, Career
D2 Armor Picker – Free Third-Party Tool
angel7marie – A Popular YouTube Star
Truck Accident Lawyer Chicago Chicagoaccidentattorney.Net
The Benefits of the Schoology BCPS